Hey folks,
I'm almost afraid/ashamed to post this, but I'm desparate so here it is. It's a bit lengthy and will be for the more advanced computer guys on here.
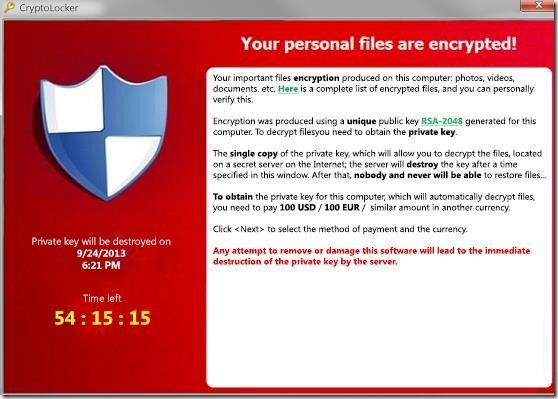
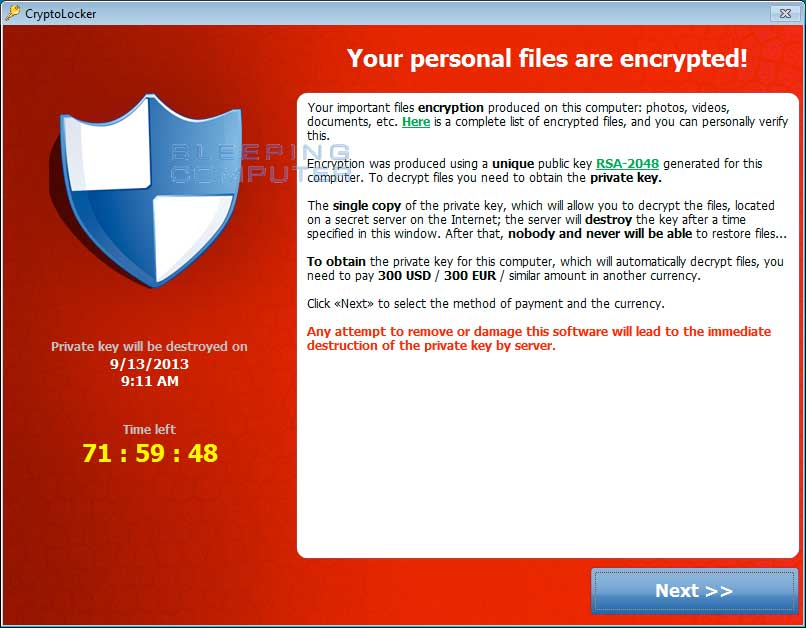
Well, I've gotten hit by a variant of the Cryptolocker type virus! But it hasn't given me the full screen warning message about being infected and such. But ALL of my picture(JPG) files, MPG files, PDF, Doc, and a few other types have gotten encrypted, they now have the *filetype.enc.rtf suffixes. Only when I try to open or view a file, it only opens up in Wordpad and tells me about the file encryptions, and instructions about what to do to get them un-encrypted....ie. unzip a zipped file, and then turn off my A-V and firewall, have internet access, and run the *.exe file that was in the ZIP archive, and it's supposed to THEN instruct me about where to send a RANSOM/payment using Ukash, Safepaycard, or such that is used in Europe.
This nasty bastard has also denied my ability to access and run the Task Manager, or Regedit. I WAS running a proper A-V program, but was stupid in downloading and unzipping a file that had *.scr type files....I thought they were ScreenSaver type files....and I just tried using the "TEST" feature....not actually installing them.....but apparently they were SCRIPT type files instead!
I've read that the type of encryption that these virii use are like 1024 or 2048 bit which are essentially infeasable to try to crack!? I found a simple originally *.rtf file I had made that had been changed/encrypted, and I changed it's filename to *.txt to open it in notepad, and aside from the RTF encryption warning message, the rest of the body of the file is truly ENCRYPTED, can't make out any of it!!!
I hadn't done a recent backup of my photos and such for a while, so I'm rather pissed both at myself as well as this friggin virus/trojan!
I felt I had nothing else to loose since ALL of my photos were already encrypted both on my main C drive as well as my extra D drive....a total of over 3000 files. I had first run an AVG recovery disc and it flagged all of them, but I didn't proceed with deletion. I then tried the above instructions...BUT nothing else happened, no window opened with any type of instructions about where and how much RANSOM I would have to pay??? SO....I'm wondering if this was an ORPHAN trojan, and that perhaps interpol or such had already found and shut down the culprits and their SERVER that is normally used/accessed by the unzipped *.exe file, and so that's why I can't get any instructions, but this also means that I won't be able to get a Decyption KEY code???
ANY THOUGHTS, suggestions as to how I might be able to decrypt the files.....or just kiss them goodbye, and CLEAN the computer/Registry.....I should be able to run a CD-rom based AV boot program to remove the virus. Regrettably, this is an older computer still running WinXP SP3....has IDE drive as well as SATA, but the latest AVG recovery/rescue disc can NOT find the Main System drive/files?? An older AVG Recovery disc from over a year ago CAN see it, but the Registry editor program on that one is TEXT based, the newer one has a GUI, but it can't see my C: IDE drive!?!?
Anyone know of a boot CD with a GUI type registry editor on it???
From my LAPTOP, not my infected DESKTOP! T.C.
I'm almost afraid/ashamed to post this, but I'm desparate so here it is. It's a bit lengthy and will be for the more advanced computer guys on here.
Well, I've gotten hit by a variant of the Cryptolocker type virus! But it hasn't given me the full screen warning message about being infected and such. But ALL of my picture(JPG) files, MPG files, PDF, Doc, and a few other types have gotten encrypted, they now have the *filetype.enc.rtf suffixes. Only when I try to open or view a file, it only opens up in Wordpad and tells me about the file encryptions, and instructions about what to do to get them un-encrypted....ie. unzip a zipped file, and then turn off my A-V and firewall, have internet access, and run the *.exe file that was in the ZIP archive, and it's supposed to THEN instruct me about where to send a RANSOM/payment using Ukash, Safepaycard, or such that is used in Europe.
This nasty bastard has also denied my ability to access and run the Task Manager, or Regedit. I WAS running a proper A-V program, but was stupid in downloading and unzipping a file that had *.scr type files....I thought they were ScreenSaver type files....and I just tried using the "TEST" feature....not actually installing them.....but apparently they were SCRIPT type files instead!

I've read that the type of encryption that these virii use are like 1024 or 2048 bit which are essentially infeasable to try to crack!? I found a simple originally *.rtf file I had made that had been changed/encrypted, and I changed it's filename to *.txt to open it in notepad, and aside from the RTF encryption warning message, the rest of the body of the file is truly ENCRYPTED, can't make out any of it!!!
I hadn't done a recent backup of my photos and such for a while, so I'm rather pissed both at myself as well as this friggin virus/trojan!
I felt I had nothing else to loose since ALL of my photos were already encrypted both on my main C drive as well as my extra D drive....a total of over 3000 files. I had first run an AVG recovery disc and it flagged all of them, but I didn't proceed with deletion. I then tried the above instructions...BUT nothing else happened, no window opened with any type of instructions about where and how much RANSOM I would have to pay??? SO....I'm wondering if this was an ORPHAN trojan, and that perhaps interpol or such had already found and shut down the culprits and their SERVER that is normally used/accessed by the unzipped *.exe file, and so that's why I can't get any instructions, but this also means that I won't be able to get a Decyption KEY code???
ANY THOUGHTS, suggestions as to how I might be able to decrypt the files.....or just kiss them goodbye, and CLEAN the computer/Registry.....I should be able to run a CD-rom based AV boot program to remove the virus. Regrettably, this is an older computer still running WinXP SP3....has IDE drive as well as SATA, but the latest AVG recovery/rescue disc can NOT find the Main System drive/files?? An older AVG Recovery disc from over a year ago CAN see it, but the Registry editor program on that one is TEXT based, the newer one has a GUI, but it can't see my C: IDE drive!?!?
Anyone know of a boot CD with a GUI type registry editor on it???
From my LAPTOP, not my infected DESKTOP! T.C.



Comment